
Navigating the CrowdStrike Outage Lessons and Insights for Business Continuity […]
LEARN MORE
How to Use Copilot with Office 365 Applications In today's […]
LEARN MORE
Get Started with Copilot Webinar Series! Our new get started […]
LEARN MORE
San Diego Managed Services that Unleash Business Potential San Diego […]
LEARN MORE
A Comprehensive Overview of Managed IT Services by Managed Solution […]
LEARN MORE
Microsoft Dynamics 365 Integration Overview Managed Solution partners with HubSpot […]
LEARN MORE
Managed Solution Earns 2024 Great Place To Work Certification™ San […]
LEARN MORE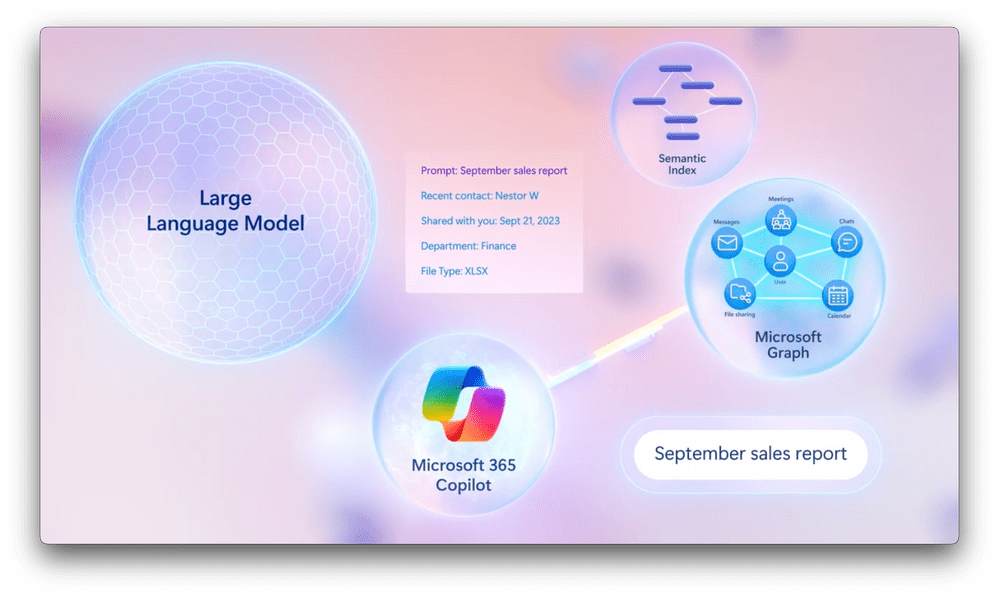
How to Connect External Data with Copilot In the […]
LEARN MOREChat with an expert about your business’s technology needs.