What You Need to Know About Zero Trust Security and AI
Discover how Microsoft uses AI for Zero Trust strategy and how their Zero Trust AI solutions work together to safeguard data, empower secure AI adoption, and outpace evolving cyberthreats.
Table Of Contents
- The New Era of Intelligent Security
- What Is Zero Trust? Definition and Foundational Pillars
- Why Zero Trust Is Reshaping Cybersecurity
- Microsoft’s Zero Trust Model: Architecture and Tools
- Zero Trust Meets AI: The New Security Partnership
- Partnering with Experts for Zero Trust Success
- The Future of Secure AI and Zero Trust
The New Era of Intelligent Security
The rise of AI has reshaped cybersecurity and digital transformation alike. As organizations embrace AI to enhance productivity, they must also address a growing array of new threats. The most effective way to manage both opportunities and risks is by uniting AI for Zero Trust into a single, cohesive defense strategy.
AI is becoming an intrinsic part of the Zero Trust model, helping organizations detect, predict, and respond to threats with unprecedented speed and accuracy. At the same time, Zero Trust provides the governance, verification, and access controls needed to ensure secure and responsible AI adoption.
Microsoft is leading this convergence through the Microsoft Zero Trust approach, embedding AI as a key layer within its Zero Trust architecture. The result is a proactive, intelligent security framework that continuously adapts to emerging threats and enables innovation without compromising protection. It’s about harnessing Zero Trust and AI to outpace cyberthreats and setting the new standard for enterprise resilience.
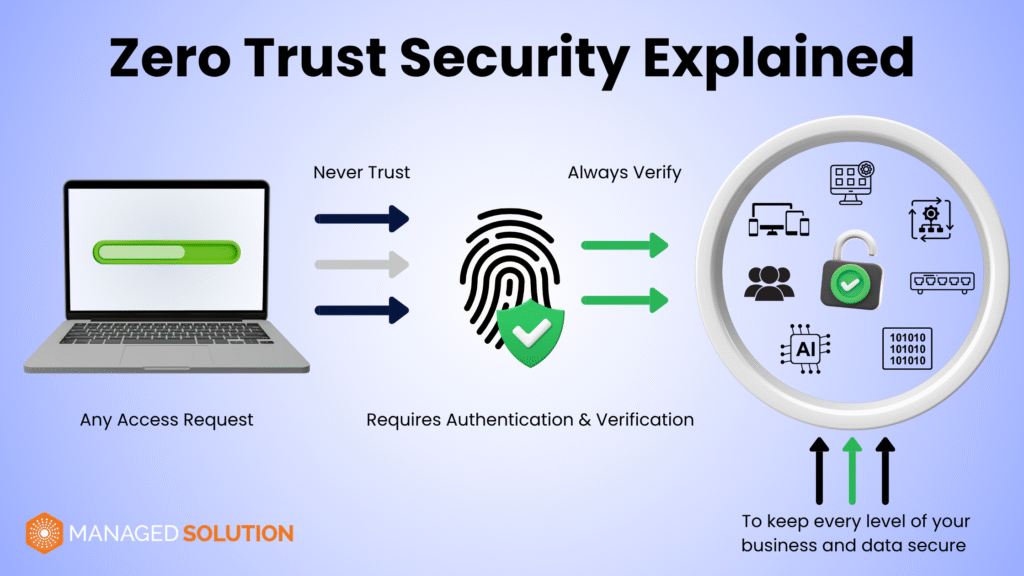
What Is Zero Trust? Definition and Foundational Pillars
Zero Trust is not a product or a single solution, but rather a security philosophy and architectural model grounded in the principle: never trust, always verify. Traditional perimeter-based security assumed that anything inside the network could be trusted. Zero trust security challenges that assumption by treating every request, regardless of origin, as potentially untrustworthy.
The Three Foundational Pillars
- Verify explicitly
Every access request is evaluated based on multiple contextual factors, including user identity, device health, location, workload, data sensitivity, and behavioral anomalies. - Use least-privilege access
Users and systems are granted only the permissions required to perform their specific tasks, often for a limited time. Concepts like just-in-time and just-enough access, adaptive risk-based policies, and granular controls all help minimize the impact of a potential breach. - Always assume breach
Security must be proactive, not reactive. Encrypt data end-to-end, monitor continuously, use analytics to detect abnormal activity, and design systems for rapid detection and response.
For organizations exploring how to implement Zero Trust, these principles must translate into concrete controls that span identities, devices, applications, infrastructure, networks, and data.
Why Zero Trust Is Reshaping Cybersecurity
As businesses move toward hybrid environments, cloud adoption, and remote work, the traditional network perimeter continues to dissolve. Legacy defenses built around firewalls and VPNs can no longer provide sufficient protection.
Zero Trust replaces the static, location-based security model with dynamic, data-centric verification. By validating every access request and limiting lateral movement, Zero Trust minimizes the damage of potential intrusions and provides a more adaptable defense against evolving cyberthreats.
For many organizations, Zero Trust has become the foundation of modern cybersecurity, especially in cloud and hybrid environments where boundaries are fluid and constantly changing. As Zero Trust vendors continue to innovate, Zero Trust is evolving into a scalable, AI-enhanced framework for future-ready security.
Microsoft’s Zero Trust Model: Architecture and Tools
Microsoft has built Zero Trust into the core of its security ecosystem, integrating it across Azure, Microsoft 365, and the broader Microsoft Security Stack. The Microsoft Zero Trust model aligns with eight key areas of defense that together form a unified and intelligent security architecture.
- Identity
Secure all identities, whether users, services, or devices, using strong authentication and authorization. Microsoft Entra ID (formerly Azure AD) serves as the foundation for conditional access, single sign-on, and passwordless multi-factor authentication.
- Devices and Endpoints
Evaluate the security posture of every device accessing corporate resources. Microsoft Intune and Endpoint Manager enforce compliance, while Microsoft Defender XDR detects and responds to endpoint threats, containing and remediating compromised devices.
- Applications
Control access and monitor behavior across cloud and on-premises apps. Microsoft Defender for Cloud Apps identifies shadow IT, applies adaptive policies, and enforces governance with real-time monitoring and analytics.
- Network
Zero Trust rejects automatic trust of internal networks. Microsoft employs network micro-segmentation, encryption, and advanced threat protection through Azure Firewall, DDoS Protection, and Defender with Azure Sentinel integration for real-time detection and response.
- Infrastructure
For workloads, containers, and virtual machines, Microsoft tools like Azure Security Center, Landing Zones, and Blueprint policies maintain compliance and monitor telemetry for anomalies across hybrid environments.
- Data
Microsoft’s Purview and Information Protection tools classify, label, and encrypt data across environments. This ensures that sensitive information remains governed and secure no matter where it resides.
- AI and Assistants
Microsoft extends Zero Trust to its AI ecosystem. Tools like Copilot for Security, Copilot in Defender, and Copilot in Entra apply Zero Trust principles to AI systems, ensuring responsible use, secure access, and intelligent defense against evolving threats. This layer also supports secure generative AI, ensuring organizations can innovate with confidence while maintaining privacy, compliance, and control.
- Visibility, Automation, and Orchestration
Through Microsoft Sentinel and Defender XDR, Microsoft provides unified visibility, behavioral analytics, and automated response capabilities. This allows organizations to detect anomalies and enforce policies automatically across their entire digital estate. Together, these layers create continuous, context-aware enforcement that operates seamlessly in the background, maintaining strong security without interrupting productivity.
Zero Trust Meets AI: The New Security Partnership
As organizations increasingly adopt AI, they face new challenges such as adversarial attacks, data poisoning, model theft, and AI-generated phishing or misinformation. Zero Trust provides the governance and control mechanisms needed to mitigate these risks.
Zero Trust principles strengthen AI systems by isolating models, enforcing least-privilege access, continuously monitoring for anomalies, and validating AI-generated outputs. Likewise, AI enhances Zero Trust by improving detection accuracy, automating policy enforcement, and identifying threats that might otherwise go unnoticed.
Together, they form a mutually reinforcing security model. AI brings intelligence and automation, while Zero Trust ensures structure, control, and accountability. Microsoft’s integrated Zero Trust solutions embody this balance, helping organizations protect their environments while innovating responsibly.
Moreover, Zero Trust architecture lays a strong foundation for AI adoption by enforcing rigorous data access controls, ensuring data integrity, and establishing clear accountability across systems. These principles are essential for training trustworthy AI models and deploying them securely. By embedding Zero Trust early, businesses create an environment where AI can be implemented with confidence—knowing that sensitive data is protected, user actions are verified, and systems are resilient against misuse or manipulation.
credit: Microsoft
Partnering with Experts for Zero Trust Success
Implementing a Zero Trust framework requires strategic planning, integration across tools and environments, and a deep understanding of Microsoft’s evolving security ecosystem. That’s where Managed Solution can help. As a Microsoft Cloud Partner with advanced specialization in Microsoft security, Managed Solution’s experts provide Zero Trust consulting designed to meet organizations wherever they are in their security journey. Our team helps businesses:
- Assess their current posture and identify gaps in protection
- Design and implement a tailored Microsoft Zero Trust model
- Integrate AI-driven Zero Trust solutions that enhance threat detection, automation, and compliance
- Prepare for the future of secure generative AI and responsible AI governance
Our goal is to empower organizations to confidently harness Zero Trust and AI to outpace cyberthreats while protecting their people, data, and innovation.
Ready to strengthen your security strategy?
Contact Managed Solution today to explore our Zero Trust consulting and Microsoft Security services, and start building a smarter, more resilient defense for your organization.
The Future of Secure AI and Zero Trust
As AI becomes deeply integrated into business operations, the need for AI-driven Zero Trust is only increasing. Microsoft’s innovations illustrate how intelligent systems and strict access controls can coexist to create adaptive, resilient security frameworks. By adopting the Microsoft Zero Trust model and leveraging AI for Zero Trust solutions, organizations can move from reactive defense to proactive intelligence.
This shift allows businesses to not only protect their data and operations but also safely harness the full potential of secure generative AI. In the modern threat landscape, AI-driven Zero Trust architecture is not just a strategy, but a new cornerstone of zero trust security and the future of cyber defense.
